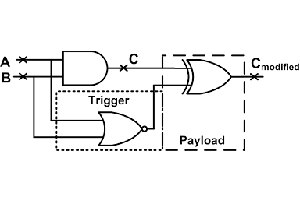
Resources
Our team of supply chain experts and researchers is dedicated to maintaining an up-to-date and valuable resource on supply chain attacks and exploits. While not exhaustive, this list offers a broad overview of the diverse attack vectors that impact the global ICT supply chain. We aim to provide insights that help you better understand the evolving landscape of cyber threats and vulnerabilities.
Please note that all information published here is derived from publicly available sources, including security research and investigative journalism. None of the content is classified or commercially sensitive; it remains entirely within the public domain.
PDFs have been captured and are periodically updated to provide a record in the event that the original source is removed.
-

Original Source: bleepingcomputer.com
-

Original Source: bleepingcomputer.com
-
-
-
-
-
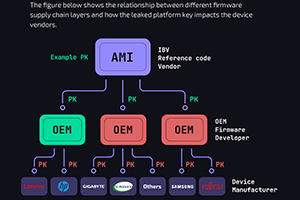
Original Source: cybernews.com
-
Original Source: bleepingcomputer.com
-
-
-
-
-
-
-
-

Original Source: zdnet.com
-
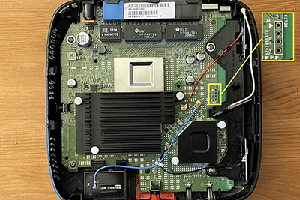
Original Source: medium.com/tenable-techblog
-
-
-

Original Source: portswigger.net
-
-
-
-

Original Source: federalregister.gov
-
-

Original Source: vice.com
-
Original Source: theintercept.com
-

Original Source: csrc.nist.gov
-
Original Source: bloomberg.com
-
-
Original Source: arstechnica.com
-
-
-

Original Source: arstechnica.com
-
-
-
-
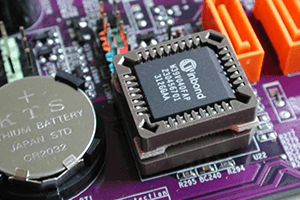
Original Source: extremetech.com
-
-
-

Original Source: tmcnet.com
-
-
-
-

Original Source: theintercept.com
-
-

Original Source: theintercept.com
-
-
-